Every Thing You Need to Know About mTLS
Contents
What is mTLS
mTLS, or Mutual TLS, is an extension of the Transport Layer Security (TLS) protocol that ensures both the client and the server authenticate each other during the TLS handshake. While traditional TLS only requires the server to present a certificate to prove its identity, mTLS requires both the server and the client to exchange and validate certificates.
mTLS steps in to address this by establishing a two-way authentication process. Both the server and the client authenticate each other using digital certificates, ensuring that both parties are who they claim to be. This mutual authentication creates a trusted communication channel resistant to impersonation and man-in-the-middle attacks.
Understanding TLS
To appreciate mTLS, it’s essential to have a fundamental understanding of TLS. TLS is the successor to Secure Sockets Layer (SSL) and works by encrypting the data transmitted between a web server and a web browser, making it unreadable to eavesdroppers. The TLS protocol involves the following key steps:
- Handshake: The client and server establish a connection and agree on the version of TLS and the encryption algorithms (cipher suite) to use.
- Server Authentication: The server presents a certificate (usually signed by a trusted CA) to prove its identity to the client.
- Key Exchange: The client and server generate session keys for encryption, often using asymmetric encryption to securely exchange these keys.
- Secure Communication: With the session keys in place, the client and server can communicate securely with symmetric encryption, where both sides encrypt and decrypt data using shared secret keys.
TLS ensures that any data transmitted between the client and server remains confidential and is not tampered with, providing integrity and privacy.
How mTLS works
mTLS enhances the standard TLS handshake process by adding an additional step where the client also presents its certificate to the server for authentication. Here’s how the mTLS handshake typically works:
- Initiation: The client begins the TLS handshake by sending a “ClientHello” message, indicating its willingness to establish a connection.
- Server Certificate: The server responds with a “ServerHello” message, followed by its certificate and a “CertificateRequest” message, which signals that the client must also provide a certificate.
- Client Certificate: The client then sends its certificate to the server. If the client does not have a certificate or the certificate is invalid, the server may terminate the connection.
- Verification: The server verifies the client’s certificate, ensuring it is signed by a trusted CA and has not expired or been revoked.
- Key Exchange and Secure Communication: Like in the standard TLS handshake, the server and client exchange keys, and secure communication begins.
During this process, both the client and the server perform cryptographic checks to ensure the other’s certificate is valid and trustworthy. If either party’s certificate fails validation, the handshake is aborted, and the communication is not established, thus preventing unauthorized access.
How to create self-signed certificate with OpenSSL
Script to generate self-signed certificate.
|
|
Step #1 - Create Root CA Certificate and Key
Step 1.1 - Generate Root CA Private Key:
We’ll generate a RSA type private key that is 2048 bits in length. Longer the key, harder it becomes to crack the key, and therefore more secure.
|
|
Step 1.2 - Generate Root CA Certificate
Now, let’s generate the CA certificate using the CA private key generated in the previous step. The certificate will be valid for next 365 days.
|
|
The above command will prompt you for additional details about your company, org, internal domain name of the CA for which the certificate is being requested.
Step #2 - Create Server Certificate and Key
Step 2.1 - Generate Server Private Key and Server CSR
The following command will create a new server private key and a server certificate signing request(CSR).
|
|
The above command will prompt you for additional details about your company, org, internal domain name of the server for which the certificate is being requested.
Step 2.2 - Server Certificate Creation and Signing using CA Key.
We’ll use the CAKey and CA cert file to sign the server CSR.
|
|
Just providing CommonName or CN in the CSR is not enough. Using CN is obsolete. You should add the SubjectAlternateName or SAN extension to the certificate. Otherwise, you may get an error shown below when using the certificate without the SAN extension.
x509: certificate relies on legacy Common Name field, use SANs instead
For added security, we should restrict the certificate to be used by a SSL/TLS/HTTPS server application only and not by any SSL/TLS/HTTPS client application. For this purpose, we’ll use the ExtendedKeyUsage key with a value of serverAuth
Step #3 - Create Client Certificate and Key
Step 3.1 - Generate Client Private Key and Client CSR
|
|
Step 3.2 - Client Certificate Creation and Signing using CA Key
We’ll use the CAKey and CA cert file to sign the client CSR.
|
|
For added security, we should restrict the certificate to be used by a SSL/TLS/HTTPS client application only and not by any SSL/TLS/HTTPS server application. For this purpose, we’ll use the ExtendedKeyUsage key with a value of clientAuth
Step #4 - Inspect the Certificates
Use the following command to dump the certificates and visually inspect various fields in the certificate.
|
|
Use following command to verify the certificate is correct.
|
|
How to setup HTTPS server and client with TLS certificate
Simple HTTPS server with mTLS
|
|
Simple HTTPS client with mTLS
|
|
Run the client and server, you will get the response log like:
|
|
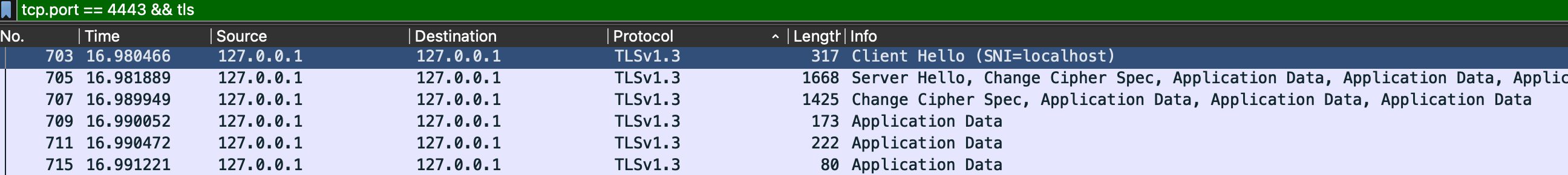
Use Wireshark to capture packages, and you’ll find:
References
- Mutual TLS Authentication - Everything you need to know
- How to create self-signed SSL TLS X.509 certificates using OpenSSL
- How to setup your own CA with OpenSSL
- How to setup HTTPS web server in Golang with self-signed SSL TLS certificate
- How to setup HTTPS client in Golang with self-signed SSL TLS client certificate
- Go HTTPS server with mTLS
Author Wenfeng
LastMod 2024-02-07
